Microsoft Edge's Application Guard is a security feature that helps protect your organization's devices and data by isolating potentially malicious websites in a separate container. There are two modes of Application Guard: standalone mode and enterprise-managed mode. In enterprise-managed mode, all new Edge windows for untrusted URLs will be opened in the Application Guard container by default. As an administrator, you can specify certain URLs as trusted, which will be opened in the user's host. All other URLs that are not specified as trusted will be considered untrusted and will be automatically opened in the Application Guard container in Edge. In this article, we will cover how to configure Application Guard in enterprise-managed mode using Group Policy or Microsoft Intune.
Enable Microsoft Defender Application Guard
The Edge Application Guard feature relies on the Microsoft Defender Application Guard feature, which must be enabled on the device in order for Edge Application Guard to be used. There are three ways to enable this feature:
Manually through the Control Panel
To manually enable the Microsoft Defender Application Guard feature, follow these steps:
Open the Control Panel.
Click on Programs and Features.
Click on Turn Windows features on or off.
Check the box next to Microsoft Defender Application Guard.
Click OK.
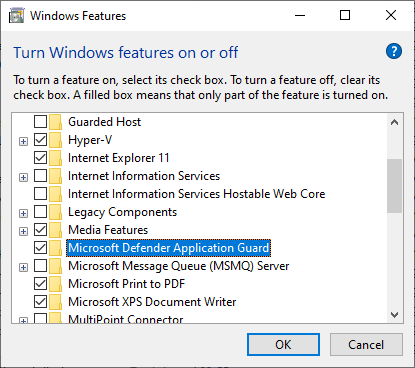
This method is typically used for testing or for enabling the feature on a single device.
Using PowerShell
If you are using Group Policy to manage the Edge Application Guard settings and want to ensure that the Microsoft Defender Application Guard feature is enabled on all devices, you can use a PowerShell script to automate this process.
To enable the feature using PowerShell, run the following command:
Enable-WindowsOptionalFeature -FeatureName Windows-Defender-ApplicationGuard -All
This method can also be used manually if desired. It is a convenient option for IT administrators who want to enable the feature on multiple devices at once.
Using Microsoft Intune
If you are using Microsoft Intune, you do not need to worry about manually enabling the feature, as it will be automatically enabled when the Endpoint Protection profile is applied. Follow these steps to create the Endpoint Protection profile:
Go to the Intune admin center and navigate to Devices > Configuration Profiles > Create profile.
Choose
Windows 10 and lateras the platform, selectTemplatesas the profile type, and chooseEndpoint protectionas the template name.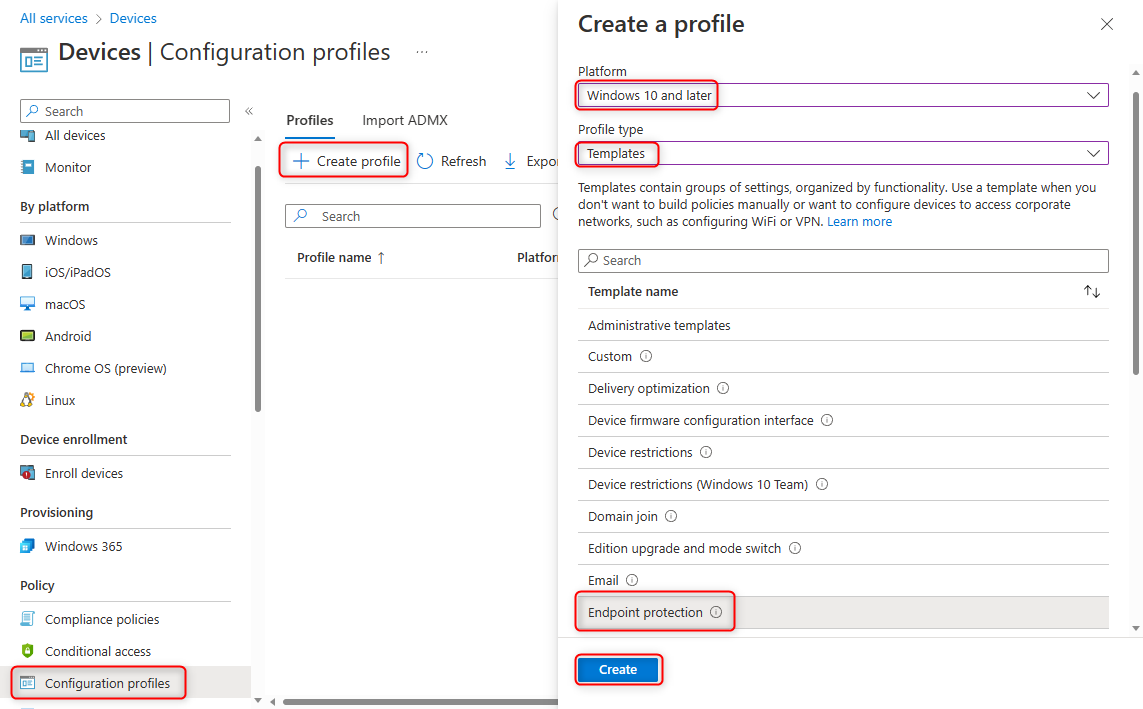
Name the profile as you prefer, for example: "Edge App Guard".
Expand the Microsoft Defender Application Guard category and click the Application Guard dropdown. Choose
Enable for Edge.Configure any additional settings as needed and click Create.
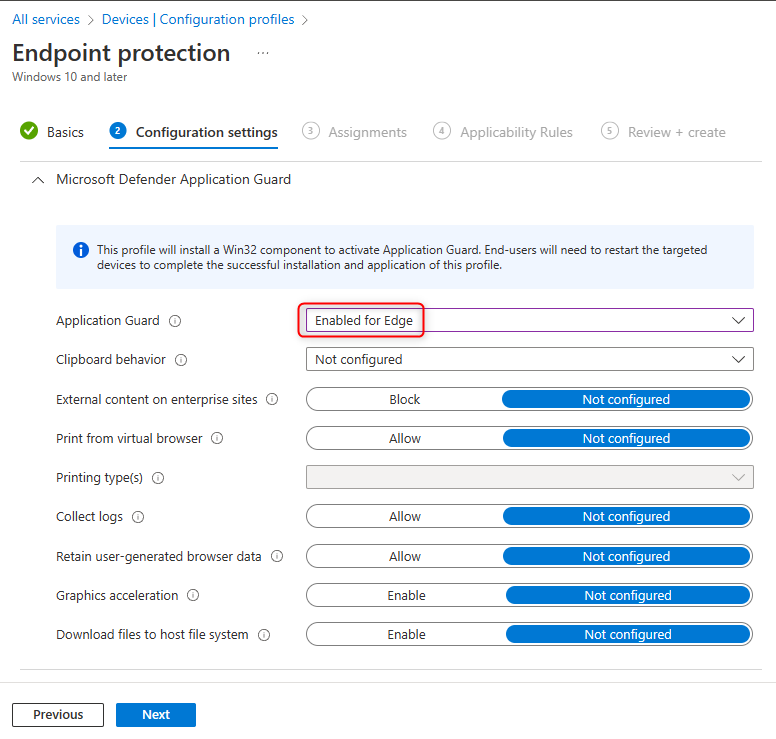
Assign the profile to the appropriate users or devices.
Enable Microsoft Defender Application Guard in Hyper-V
If you are using Microsoft Hyper-V to run virtual machines and want to enable the Microsoft Defender Application Guard feature, follow these steps:
Enable Hyper-V nested virtualization on the host machine by running the following PowerShell command as an administrator:
Set-VMProcessor -VMName "your-vm-name" -ExposeVirtualizationExtensions $trueEnsure that the virtual machine has a minimum of 8 GB of RAM.
Ensure that the virtual machine has a minimum of four cores (logical processors).
Standalone mode
After enabling the Microsoft Defender Application Guard feature, users have access to standalone mode, which can be accessed by using the New Application Guard Window option in the Edge browser's settings.
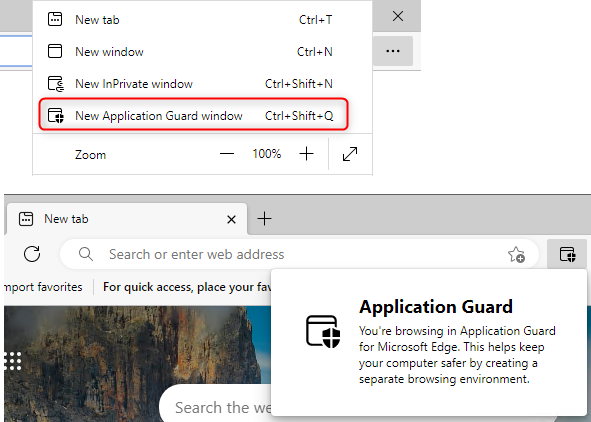
In standalone mode, users are in full control over which websites are visited within the container. However, for each website, users must manually decide whether to open it in the Application Guard container or not.
This approach provides users with a high level of control over how they use the Application Guard feature, but also increases the responsibility on the users to ensure that they are only visiting trusted websites outside the container.
It's worth noting that, in order to reduce user responsibility and increase enterprise security, enterprise environments tend to use a mode called enterprise-managed mode, where the decision of which site should open in the container and which should not, is made by the administrator.
Enterprise-managed mode and Network boundary
Enterprise-managed mode is a way for administrators to control which URLs are opened in the Application Guard container, rather than leaving this decision up to the user in standalone mode. This is done by setting up a network boundary, which defines Trusted URLs, Neutral URLs, and Untrusted URLs.
Trusted URLs are domains that are considered safe and are intended to be accessed in the user's host. They can be configured via group policy settings under: Computer Configuration -> Administrative Templates -> Network -> Network Isolation. There are two group policy settings here: Private network ranges for apps and Enterprise resource domains hosted in the cloud. Any navigation to these Trusted URLs will happen in the Microsoft Edge browser on the host machine rather than in the Application Guard environment.
Neutral URLs, on the other hand, can be configured via a single group policy setting: Domains categorized as both work and personal, also found under Computer Configuration -> Administrative Templates -> Network -> Network Isolation. This setting allows administrators to specify a list of domains that are considered both work-related and personal, and any URLs accessed from these domains will be opened in the same window in which the navigation occurred.
It's important to note that Enterprise resource domains hosted in the cloud and Domains categorized as both work and personal are both used for configuring domains, and both support wildcard formatting. Here's a table that illustrates the different formats and their meanings.
| Value | Number of dots to the left | Meaning |
|---|---|---|
contoso.com |
0 | Trust only the literal value of contoso.com. |
www.contoso.com |
0 | Trust only the literal value of www.contoso.com. |
.contoso.com |
1 | Trust any domain that ends with the text contoso.com. Matching sites include spearphishingcontoso.com, contoso.com, and www.contoso.com. |
..contoso.com |
2 | Trust all levels of the domain hierarchy that are to the left of the dot. Matching sites include shop.contoso.com, us.shop.contoso.com, www.us.shop.contoso.com, but NOT contoso.com itself. |
Any URL that is not configured as a Trusted or Neutral URL is considered an Untrusted URL. In enterprise-managed mode, all navigation to Untrusted URLs will automatically open in the Application Guard container.
For example, if we configure .microsoft.com in Enterprise resource domains hosted in the cloud as a Trusted URL and .bing.com in Domains categorized as both work and personal as a Neutral URL, the following will happen:
- Navigating to
www.microsoft.comwill happen in Microsoft Edge on the host machine, because it is a Trusted URL. - Navigating to
www.bing.comin this Edge window will also happen in the same Edge window on the host machine, because it is a Neutral URL. - If you then navigate to
www.google.com(an untrusted URL), it will open in an Application Guard Edge window in the container. This is becausewww.google.comis an untrusted URL. - If you then navigate to
www.bing.comin this Application Guard Edge window, the navigation will stay in the Application Guard Edge window becausewww.bing.comis a Neutral URL.
Configuring Network boundary using Intune
In addition to using Group Policy to configure network boundary, it is also possible to use Microsoft Intune to manage Application Guard settings. Here are the steps to configure Trusted and Neutral URLs using Intune:
In the Intune admin center, navigate to Devices > Configuration Profiles > Create profile. Choose
Windows 10 and lateras the platform, selectTemplatesas the Profile type, and chooseNetwork boundaryas the Template name.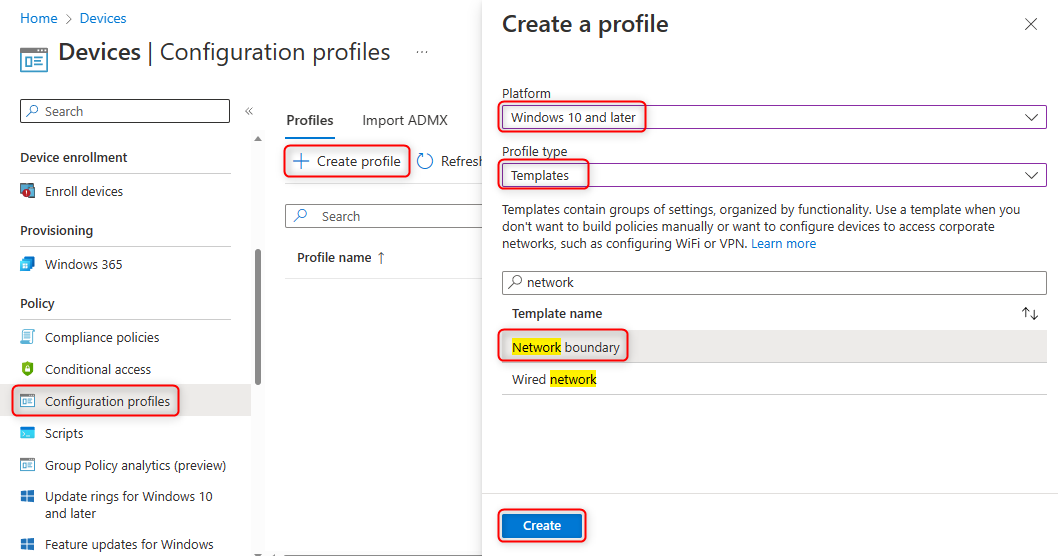
Name the profile as desired, for example Network isolation.
In the next page, there will be several options for configuring different boundary types with different values.
The
Cloud resourcesboundary type maps to theEnterprise resource domains hosted in the cloudgroup policy setting, where you can define domains as Trusted URLs.The
IPv4 rangeandIPv6 rangeboundary types map to thePrivate network ranges for appsgroup policy setting, where you can define IP ranges as Trusted URLs.The
Neutral resourcesboundary type maps to theDomains categorized as both work and personalgroup policy setting, where you can define domains as Neutral URLs.
Assign the profile to the appropriate users or devices.
Once you have configured the network boundary profile in Intune, you will be able to apply it to devices and users in your organization, allowing you to manage the Application Guard settings centrally. Just as like when you configure with Group Policy, Intune also support wildcard character and format follow the table above.
Enabling Enterprise-managed Mode with Group Policy
When using Group Policy to configure Application Guard settings, it's important to make sure that the policy Turn on Microsoft Defender Application Guard in Managed Mode is enabled. This policy can be found at Computer Configuration -> Administrative Templates -> Windows Components -> Microsoft Defender Application Guard. The value of the policy should be set to 1. Enable Microsoft Defender Application Guard for Microsoft Edge ONLY. This will ensure that Microsoft Edge will use enterprise-managed mode, instead of standalone mode.
Note: The category Computer Configuration -> Administrative Templates -> Windows Components -> Microsoft Defender Application Guard is only available in Windows 10/Windows 11 clients, and may not be present in the Group Policy Editor when using a Windows Server machine as a GPO management server. In order to enable this setting in a Windows Server environment, you will need to copy the files C:\Windows\PolicyDefinitions\AppHVSI.admx and C:\Windows\PolicyDefinitions\en-US\AppHVSI.adml from a Windows 10/11 machine to the same path on the Windows Server machine (replacing en-us with the appropriate language for your environment).
It's worth noting that when using Intune, there is no additional configuration necessary for this setting as it was already enabled in the previous steps of enabling Microsoft Defender Application Guard.
Proxy support
By default, the Application Guard Edge browser uses the same proxy settings as the Edge browser on your host machine. However, if you do use a proxy server for browsing websites, you need to pay attention to the following points:
- The proxy server or PAC server must be a fully-qualified domain name (FQDN). A simple IP address will not work.
- The proxy servers or PAC server must be a neutral resource listed in the
Domains categorized as both work and personalpolicy. For example, if you have configuredhttp://pacserver/proxy.pacas your PAC script, and the script returns the proxy serverPROXY itproxy:8080, you must add bothpacserveranditproxyto theDomains categorized as both work and personal policyas Neutral sites.
Dual proxy
It is also possible to configure a different proxy setting for the Application Guard Edge browser than what is used by the host machine. To do this, you can enable the group policy setting Application Guard Container Proxy from Computer Configuration / User Configuration -> Administrative Templates -> Microsoft Edge -> Application Guard settings. You can check Application Guard Container Proxy for more detailed usage.
You can also configure the same group policy setting using Microsoft Intune by adding an Administrative Template configuration profile. The setting location is the same as mentioned above.
Transferring files between host and Application Guard container
Due to the isolated environment of the Application Guard container, the file system is separate from the host. As a result, files cannot be shared by default. This section will describe the ways in which files can be transferred between the host and the Application Guard container.
Method 1: Using Group Policy
One way to transfer files is by enabling the following Group Policy setting:
- Setting name: Allow files to download and save to the host operating system from Microsoft Defender Application Guard
- Location: Computer Configuration -> Administrative Templates -> Windows Components -> Microsoft Defender Application Guard
Once this setting is enabled, it is necessary to restart the host machine or the Application Guard Container Service for the changes to take effect. After that, files downloaded in the Edge Application Guard container will be saved in a folder called "Untrusted Files". This folder will be mapped to the host at %userprofile%\Downloads\Untrusted Files. The host machine can then access this folder to copy files to the container or to read files generated by the container.
Method 2: Using hcsdiag.exe
Another way to transfer files is by using the Hyper-V Host Compute Service Diagnostics Tool (hcsdiag.exe), which is built-in on Windows.
First, start an Edge Application Guard session. Then, run cmd as an administrator on the host machine, and execute:
hcsdiag list
This will give you a list of currently running Application Guard containers. Look for the Running HVSI and note down its GUID (for example, in the example below it is: 8F46B84C-9290-40DB-A0FE-BD387D81F2E6).
C:\Windows\system32>hcsdiag list
8f46b84c-9290-40db-a0fe-bd387d81f2e6
VM, Running, 8F46B84C-9290-40DB-A0FE-BD387D81F2E6, HVSI
b2407697-4336-4f2e-8ee2-663503993471
VM, SavedAsTemplate, B2407697-4336-4F2E-8EE2-663503993471, CmService
Then, you can use the hcsdiag share command to map a host folder to a container folder, thus enabling file transfer:
hcsdiag share 8F46B84C-9290-40DB-A0FE-BD387D81F2E6 c:\temp c:\temp-on-host
This command maps the host folder c:\temp to the container folder c:\temp-on-host.
After executing this command, we can also use following command to open the file explorer and access the C drive within the container. We should then see a directory named temp-on-host.
hcsdiag exec -existinglogin -user wdagutilityaccount 8F46B84C-9290-40DB-A0FE-BD387D81F2E6 explorer c:\
If we only want to transfer a single file, we can also use hcsdiag read or hcsdiag write to read files from or write files to the app guard container. For example, the following command reads a file from the container and saves it on the host:
hcsdiag read 8F46B84C-9290-40DB-A0FE-BD387D81F2E6 c:\temp\file.txt c:\temp-on-host\file.txt
Similarly, you can use the hcsdiag write command to write files from the host to the container.
hcsdiag write 8F46B84C-9290-40DB-A0FE-BD387D81F2E6 c:\temp-on-host\file.txt c:\temp\file.txt
This method provides a fine-grained way to transfer files between the host and the Application Guard container and is useful in cases where only a few files need to be transferred.
edge://application-guard-internals/
The edge://application-guard-internals/ page is a built-in page in Edge that allows you to check the current status of Application Guard, as well as provides a tool for checking the trust level of different URLs.
This page can be accessed by typing edge://application-guard-internals/ in the Edge browser's address bar. It will give you an overview of whether Application Guard is currently enabled or disabled and whether the current browsing session is using the Application Guard container or the host browser.
It also includes a tool for checking the trust level of different URLs. You can enter a URL into the tool and it will tell you if it is considered a Trusted, Neutral or Untrusted site according to the current Application Guard policy.
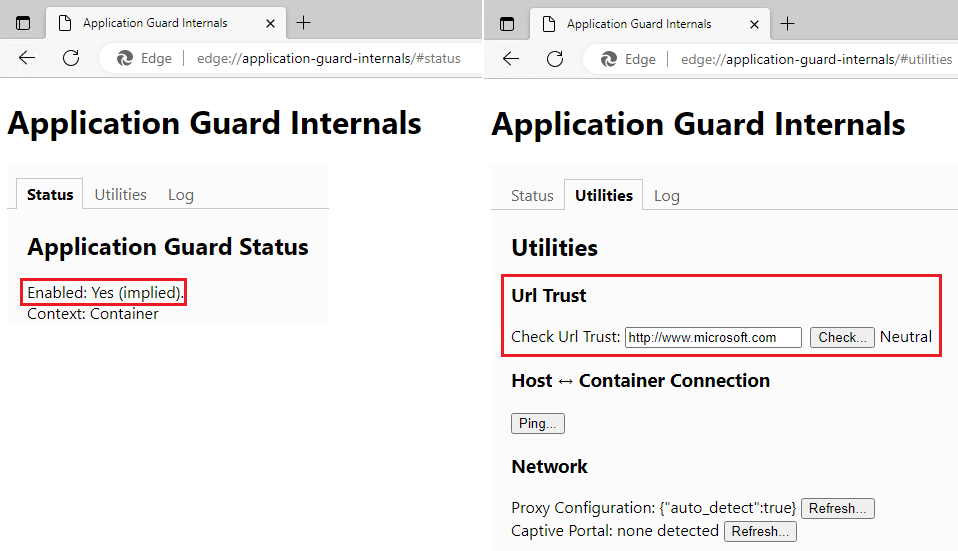
This page is useful for developers, IT professionals and administrators as they can quickly check the status of Application Guard and the trust level of different URLs without having to dig through settings or use other tools.
IE Mode Supportability in Application Guard
Internet Explorer (IE) mode is a feature in Edge that allows certain websites to be opened in IE instead of the Edge engine. However, when using Microsoft Defender Application Guard, it is not possible to use IE mode. Even if a website is configured to open in IE mode on the host machine and the website belongs to an untrusted category, it will still open in the native Edge mode within the Application Guard container. Additionally, there is no way to manually switch to IE mode within the Application Guard container.
It should be noted that IE mode is primarily intended for older, internal websites that are often trusted, while Application Guard is primarily used for untrusted URLs. As a best practice, websites configured to open in IE mode should also be configured as Trusted in network isolation settings. This ensures that these IE mode websites will continue to open in IE mode on the host machine, while also providing an added level of security using Application Guard for untrusted URLs.