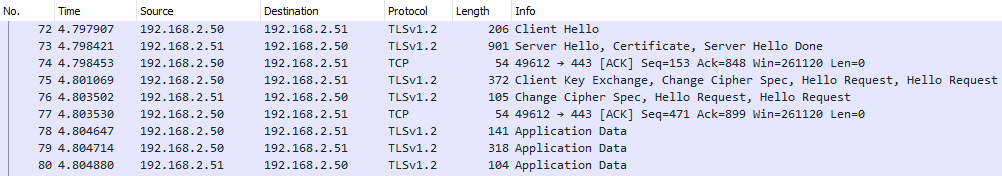
I was recently researching HTTP/2. However I can only see encrypted network packets in Wireshark because all browsers only support HTTP/2 that run over TLS. Actually Wireshark does provide some settings to decrypt SSL/TLS traffic.
Using the private key of a server certificate for decryption
The first method is: Using the private key of a server certificate to decrypt SSL/TLS packets.
Export the private key of a server certificate from an IIS server
First, we need to export the private key from the web server, take the IIS server as an example here.
Open the server certificate of an IIS website, click Details tab, click Copy to File....
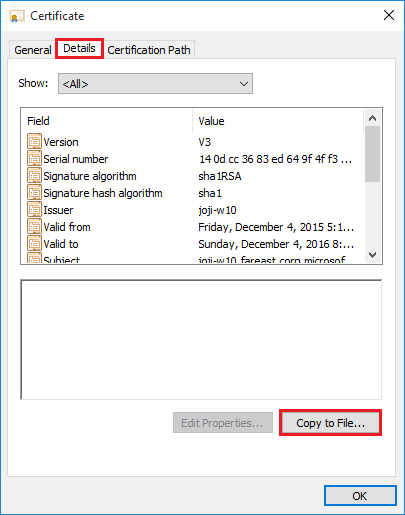
Click Next in the wizard, select Yes, export the private key, then click Next.
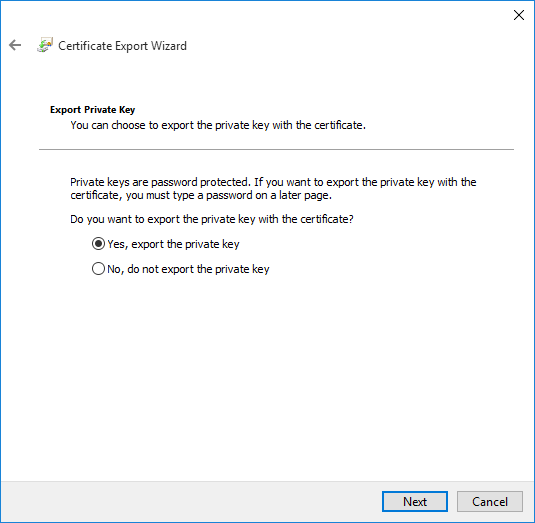
Choose Personal Information Exchange - PKCS # 12 (.PFX), leave the three checkboxes unchecked, click Next.
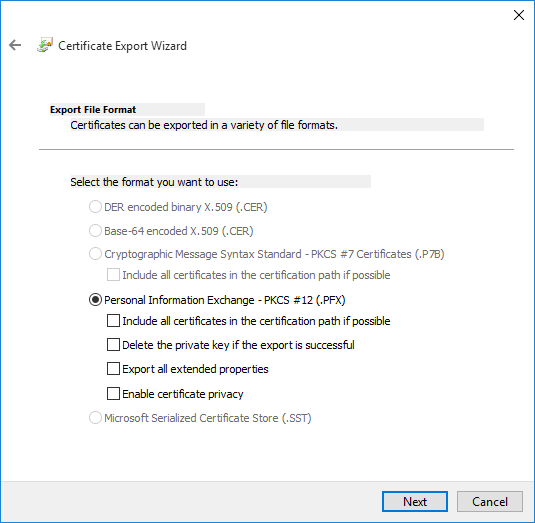
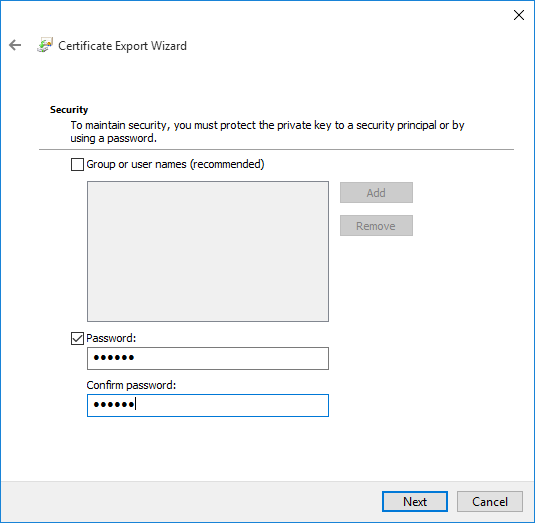
Check Password and set a password, click Next and then export the PFX file.
Configure Wireshark to use the private key for decryption
After having the PFX file, we can configure Wireshark to use the private key to decrypt SSL/TLS packets. You can configure it from either client side or server side, depending on where you view or capture the network traffic.
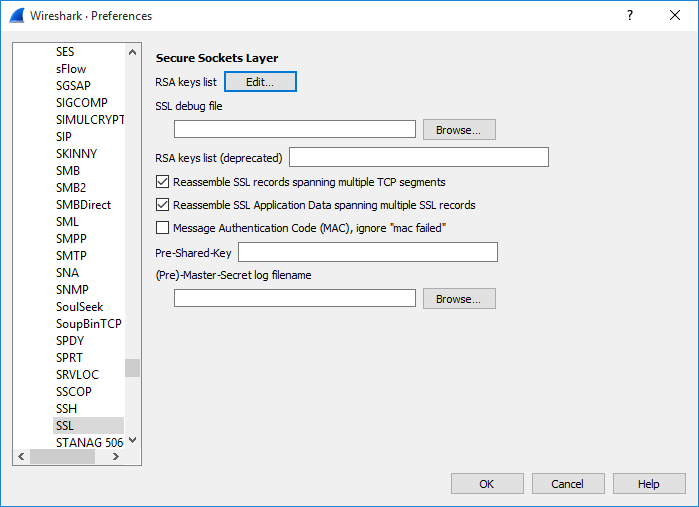
In Wireshark menu, go to: Edit -> Preferences....
Expand Protocols -> SSL, click the Edit button after RSA key lists.
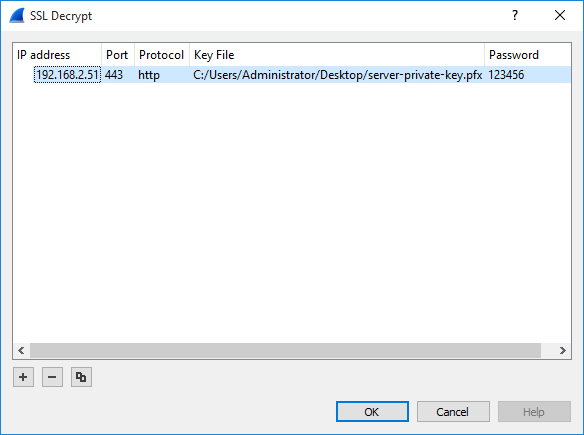
Configure as below:
- IP address: Target server IP address, you can input "any" as well.
- Port: The general port number of HTTPS is: 443.
- Protocol: http
- Key File: Select the PFX file you just exported.
- Password: The password of the PFX file.
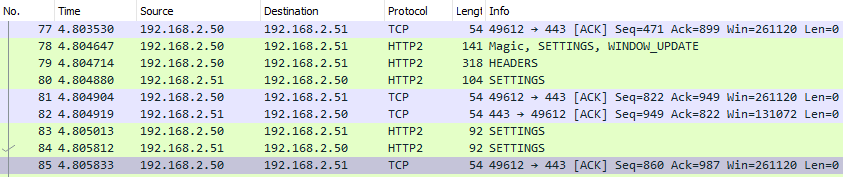
After that, the current viewing trace or the future captured trace will be decrypted as expected.
If Wireshark still doesn't decrypt the TLS/SSL packets, then the SSL session may be using a Diffie-Hellman cipher.
Disable the Diffie-Hellman cipher
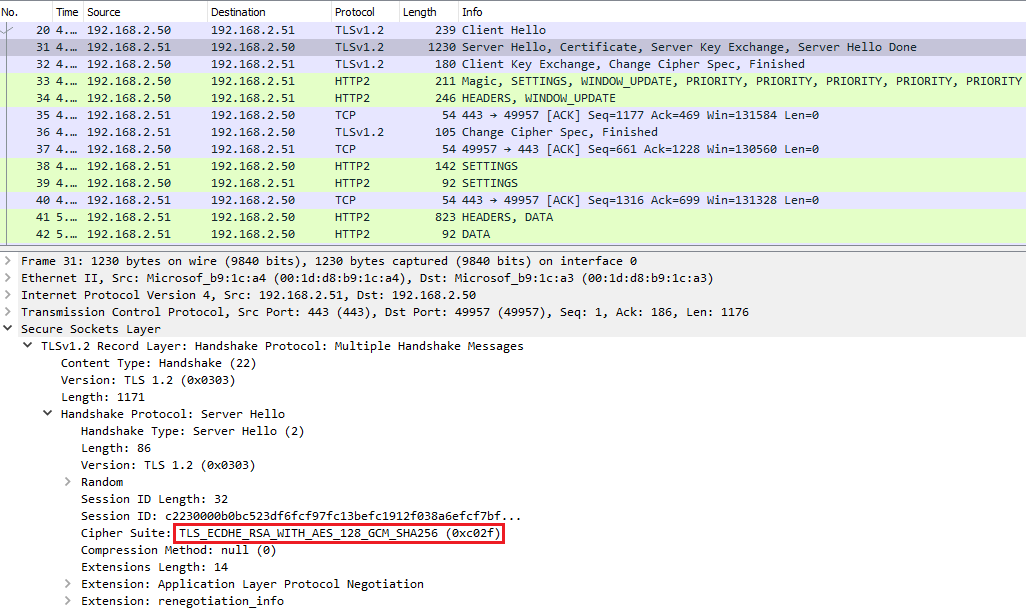
We can confirm an SSL session is using a Diffie-Hellman cipher if the Cipher Suite value of the Server Hello message contains "ECDHE" or "DHE".
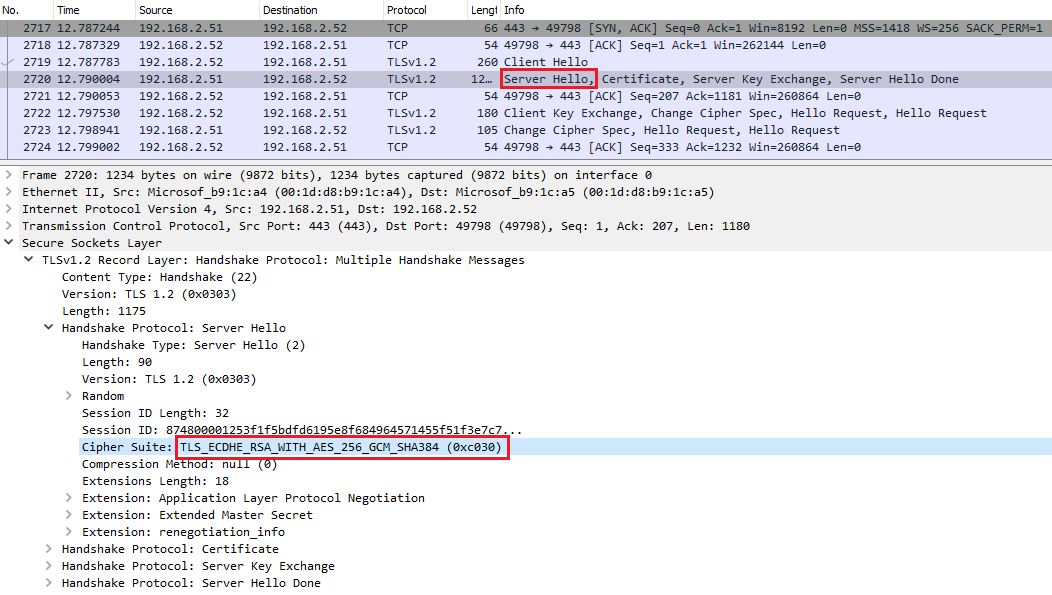
The session key is transferred encrypted with a dynamically generated key pair (instead of encrypted with the public key from the certificate) if the SSL session is using a Diffie-Hellman cipher. The solution is to disable Diffie-Hellman from the client or the server. I would recommend to disable it from the client so that we can keep the server secure.
Following are the methods to disable the Diffie-Hellman cipher from three different browsers in Windows client and the method to disable the Diffie-Hellman cipher from an IIS server. You can choose either one of them to ensure the SSL session does not use a Diffie-Hellman cipher.
Disable the Diffie-Hellman cipher for Internet Explorer
Run gpedit.msc to open Local Group Policy Editor.
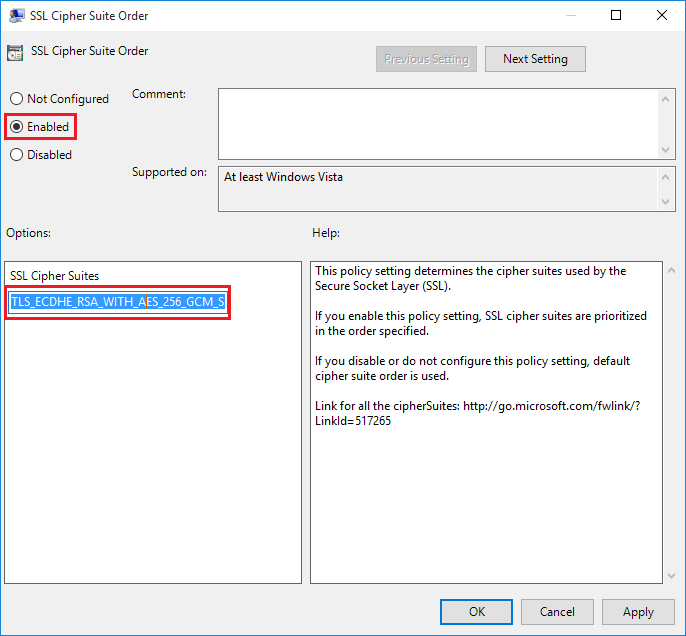
Edit setting: Computer Configuration -> Administrative Templates -> Network -> SSL Configuration Settings -> SSL Cipher Suite Order.
Enable the setting and copy the default cipher suite order from the textbox to notepad or text editor.
Remove all the ciphers that contain "ECDHE" or "DHE", please keep all the ciphers in one line.
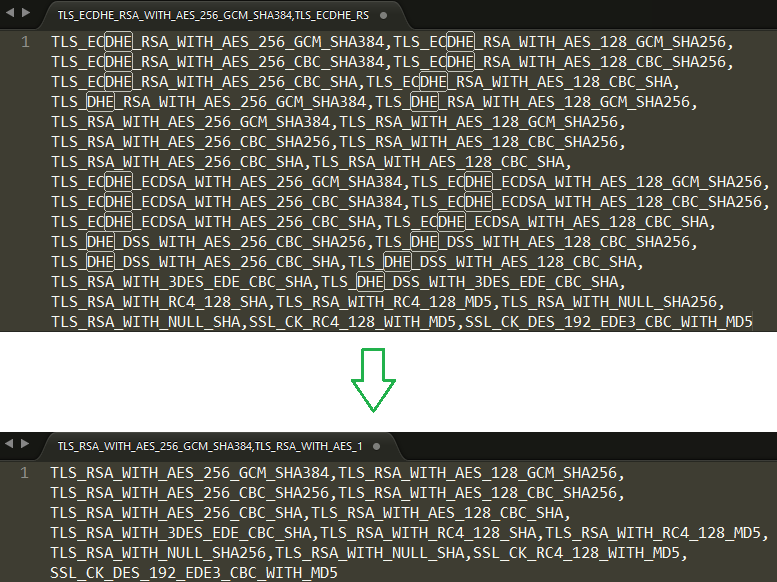
Replace the default value with the new value, click OK to save the setting, then reboot the PC.
After reboot, we can see that the Cipher Suites value in IE Client Hello message does not contain any Diffie-Hellman ciphers and Wireshark is able to decrypt the SSL/TLS packets.
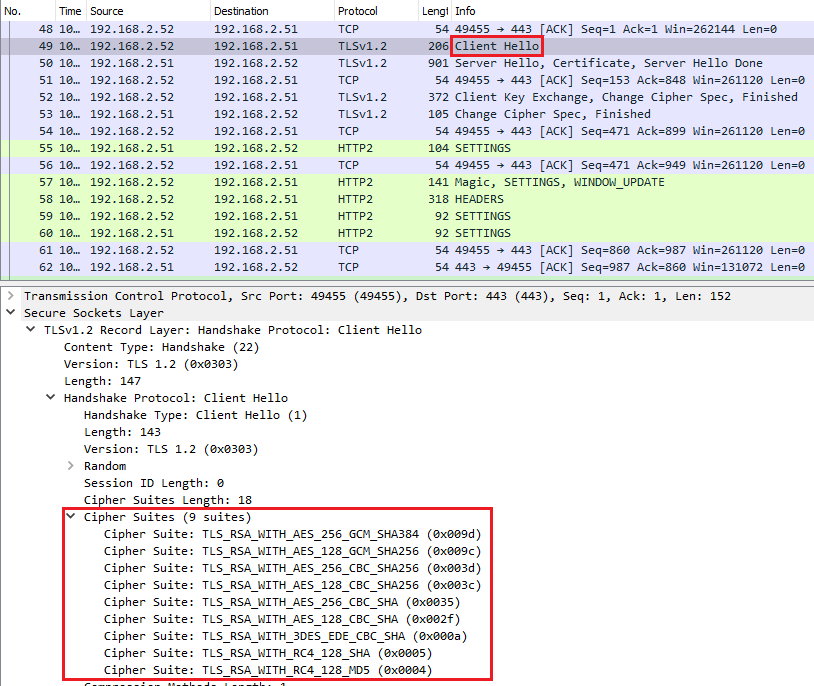
Disable the Diffie-Hellman cipher for Chrome
View the default Cipher Suites list from the Client Hello message of Chrome.
Cipher Suites (15 suites) Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b) Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) Cipher Suite: TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x009e) Cipher Suite: TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (0xcc14) Cipher Suite: TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (0xcc13) Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a) Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) Cipher Suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039) Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009) Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x0033) Cipher Suite: TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c) Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035) Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f) Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)Append all the ciphers that contain "ECDHE" or "DHE" in hex to command line parameter:"--cipher-suite-blacklist" and launch Chrome with this parameter, like:
c:\Program Files (x86)\Google\chrome\Application\chrome.exe --cipher-suite-blacklist=0xc02b,0xc02f,0x009e,0xcc14,0xcc13,0xc00a,0xc014,0x0039,0xc009,0xc013,0x0033
After that, we can see that the Cipher Suites value in Chrome Client Hello message doesn't contain any Diffie-Hellman ciphers.
Cipher Suites (4 suites) Cipher Suite: TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c) Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035) Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f) Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)
Disable the Diffie-Hellman cipher for Firefox
Launch Firefox, navigate to "about:config" from address bar, search "dhe", double click all the Diffie-Hellman ciphers to change the Value to false, restart Firefox to take effect.
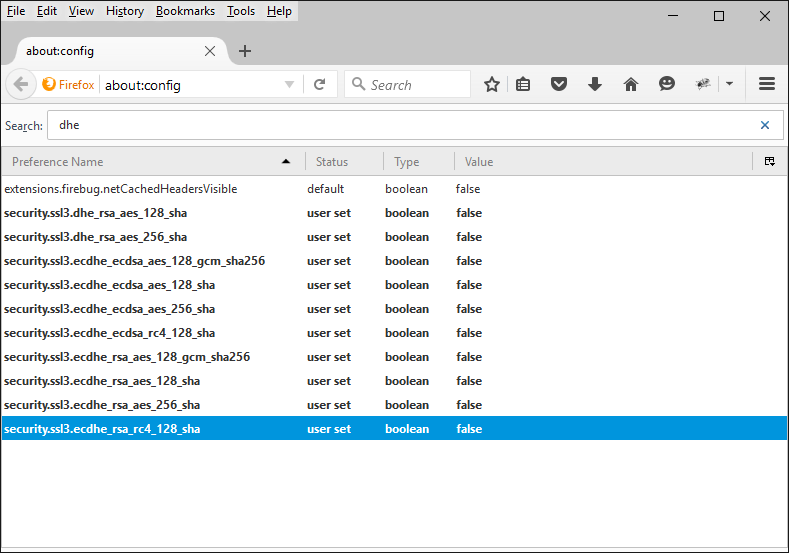
Disable the Diffie-Hellman cipher for IIS server
Run regedit as administrator, edit:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002\Functions.
Remove all the ciphers that contain "ECDHE" or "DHE".
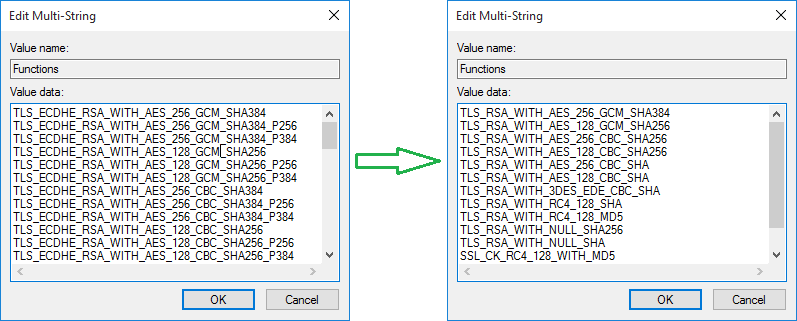
Save the change and reboot the server to take effect.
Using SSLKEYLOGFILE
The second method to decrypt SSL/TLS packets is setting an environment variable called SSLKEYLOGFILE that points to a writable text file. Chrome and Firefox will look for the variable when they start up. If it exists, the browser will write the values used to generate TLS session keys out to that file. We can configure Wireshark to read this file to decrypt SSL/TLS packets.
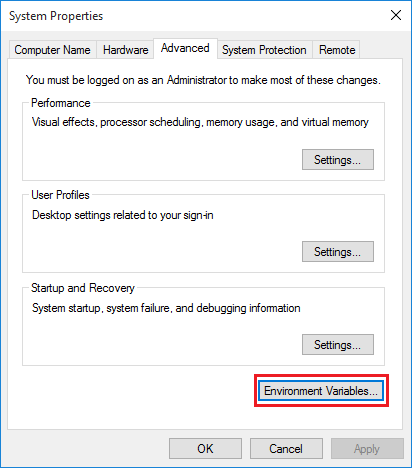
Right click Computer/This PC, view Properties, open Advanced system settings, view Advanced tab, click Environment Variables....
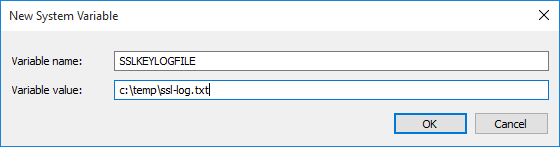
New a System variable.
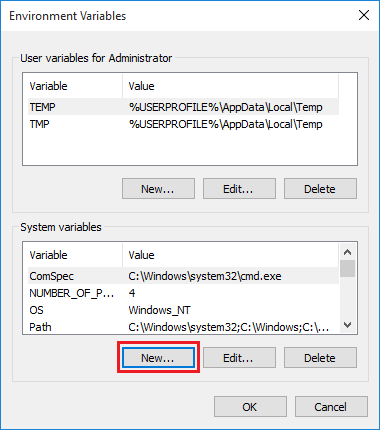
Name the variable as:SSLKEYLOGFILE, point it to a writable text file. You have to create the folder in advance, the text file can be auto generated when you launch Chrome or Firefox.
In Wireshark, go to:Edit -> Preferences....
Expand Protocols -> SSL, set (Pre)-Master-Secret log filename to the same text file.
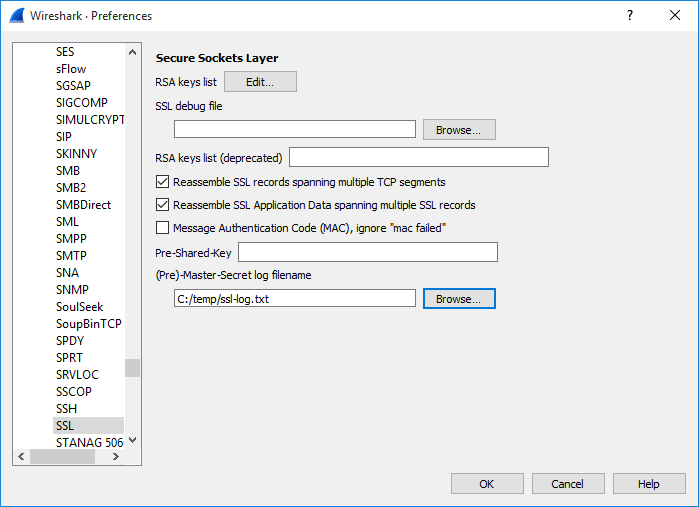
Click OK. Now Wireshark can decrypt HTTPS traffic.
Summary
This article introduces two methods to decrypt SSL/TLS trace in Wireshark, you can evaluate the pros and cons of them to choose the best method for you.
The private key of the server certificate
Pros:
- Can be used from either client side or server side.
- Supports all kinds of browsers.
Cons:
- Needs to have access to the server certificate.
- Does not support Diffie-Hellman ciphers.
SSLKEYLOGFILE
Pros:
- Supports Diffie-Hellman ciphers.
- No need to access the server certificate.
Cons:
- Can only be used from client side.
- Supports only Chrome and Firefox.